This is a report for the penetration testing cource taught by Tero Karvinen
CinCan
Date: 26-04-2020
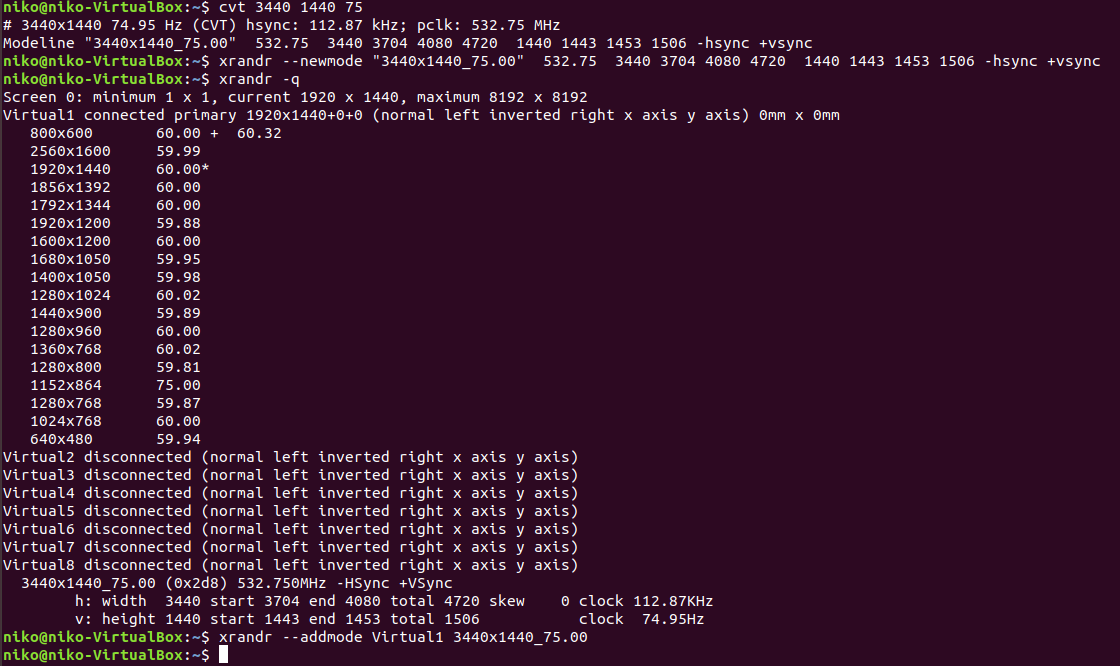
I decided to try setting up CinCan in advance and used a fresh Ubuntu 18.04 for it. Since its a fresh install there is a few things to do first. I started my fixing the display resolution using a few commands seen in the image. Note from the future: I realized that installing guest additions fixes the resolution automatically
After that i started by doing the usual sudo apt update and upgrade to make sure everything is up to date. I also installed vim and tmux then ran
echo 'set -g default-terminal "screen-256color"' > ~/.tmux.conf
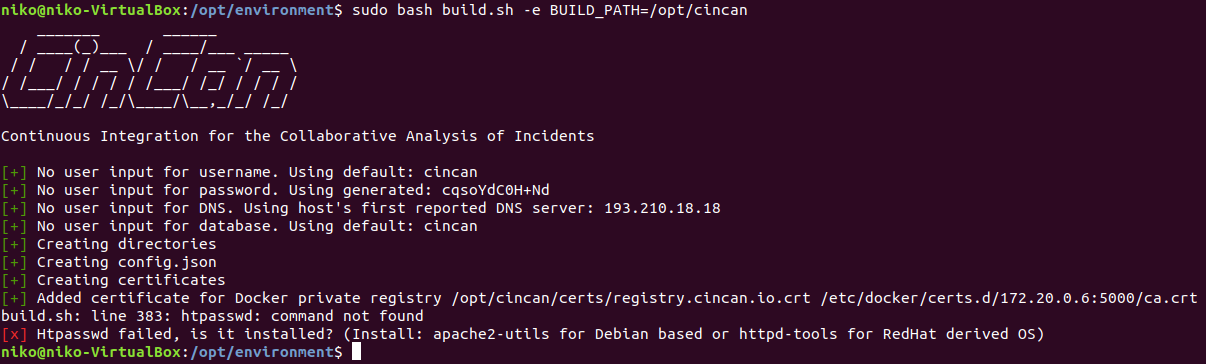
sudo bash build.sh -e BUILD_PATH=/opt/cincan
Going into /opt/cincan/build and trying to run the docker compose command it gave another error. After some troubleshooting i figured out that the required version of docker-compose is 1.18.0+ despite the README file saying that version 1.17.1 is required (which i had). I went to the docker-compose github page and chose to use version 1.25.4
Docker-Compose Versions > https://github.com/docker/compose/releases
I used these commands to install it after removing the old version using
sudp apt remove docker-compose
curl -L https://github.com/docker/compose/releases/download/1.25.4/docker-compose-`uname -s`-`uname -m` -o /usr/local/bin/docker-compose
chmod +x /usr/local/bin/docker-compose
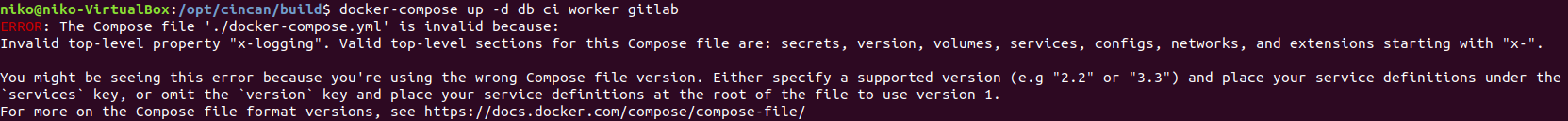
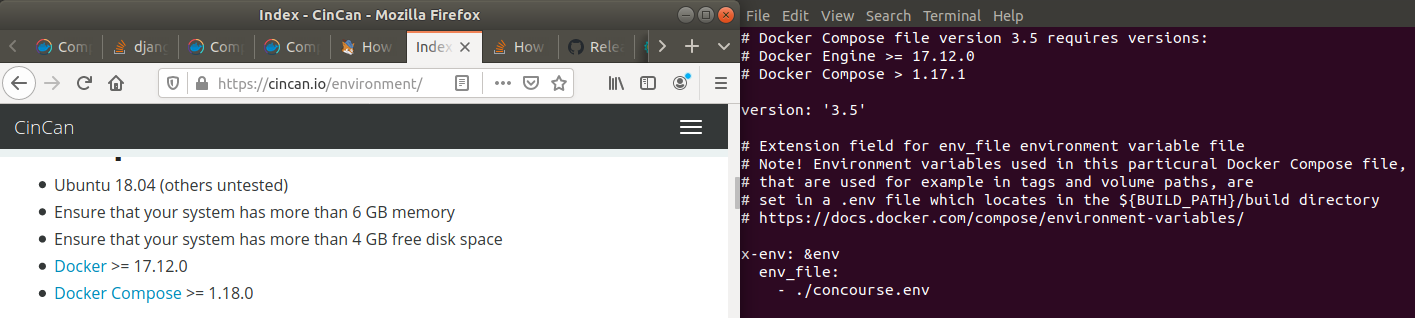
After fixing the issues with docker compose doing the docker compose command gave some error saying that docker is runnung in an unexpected location. I had been trying to fix if earlier so i might have broken something so i just re-installed it by following the steps on dockers site after which the docker compose command ran as expected. https://docs.docker.com/engine/install/ubuntu/
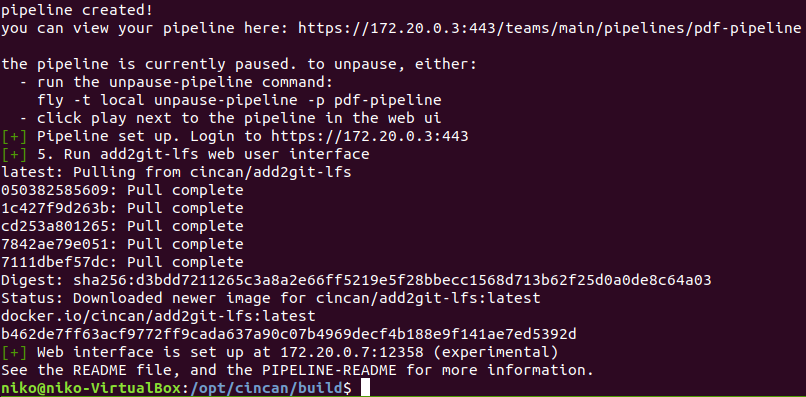
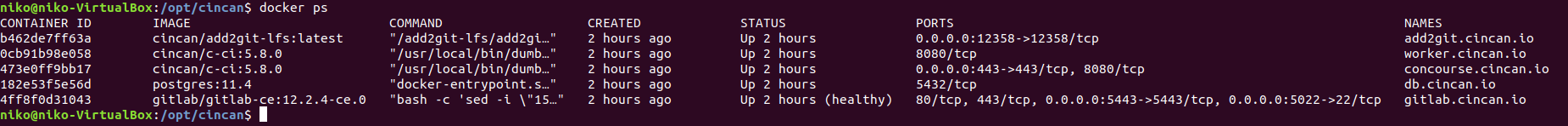
Navigating to https://172.20.0.3 i got to the concourse page. Took me a while to figure out the credentials but i eventually looked at the README file properly and found the credentails to log in with.
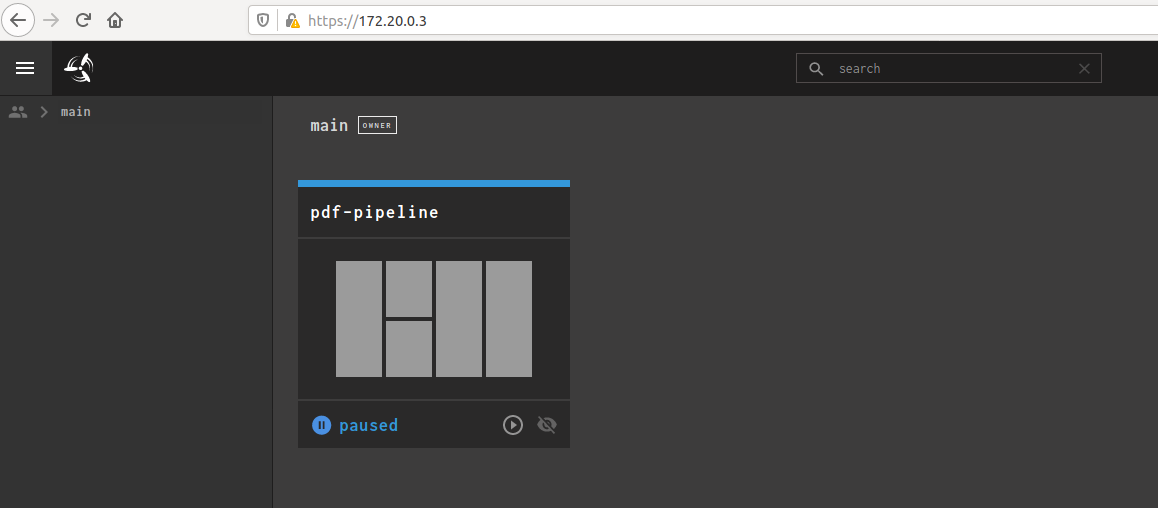
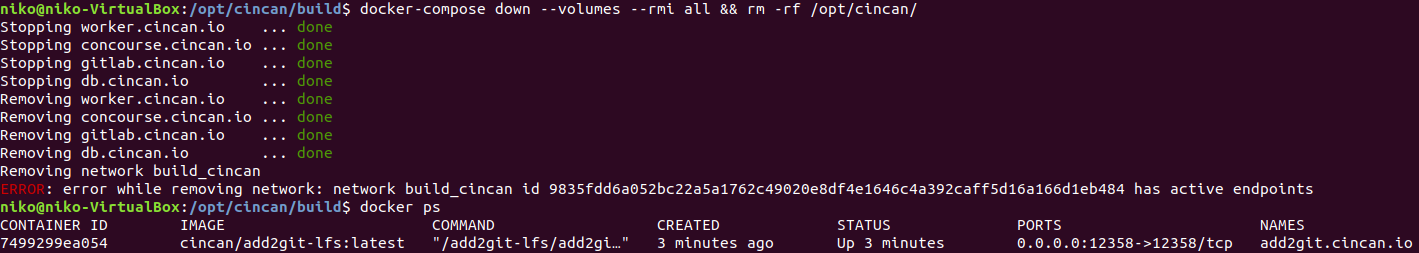
Actually closing everything down also gave me some error but this is probably enough initial testing for now.
H4
We had a CinCan workshop that i am going to be reporting here. The workshop ended up being pretty messy and im writing this from memory so i hope ill manage to make something out of this. We started by simply installin cincan-command using pip with
pip3 install cincan-command --user
export PATH=$PATH:$HOME/.local/bin
sudo bash
cincan run cincan/eml_parser mail.eml | python -m json.tool > output.txt
cincan run cincan/eml_parser:latest-stable -e zip new_payment.eml
To try cincan on some other samples i downloaded some spam mail from my email to look at. I chose an email that was sent supposedly from bentley and used eml parser to look at the data. Looking at the header it was obviously not sent form bentley but form aliya4@mukaasedmv.com. The email itself was saying that i have been invited to join something and a link to click. This link is obviously malicious so i opened it in a VM that i dont use to login to anything. Opening this link just redirects to some scetchy cash grabbing dating site so its safe to assume this spam mail is just trying to get people to create users on the site.
Cincan seems like an interesting tool so far but it is hard to say at this point what i could realistically use it for. I do really like that just trying to use a tool pulls the image if you dont already have it so you wont be in a situation where you try to use a tool only to realize that you dont have it, go install it and only then actually use it. Also running these tools in a docker container seems great to ensure that these tools work whatever machine you are running them on. Seems like cincan would be a great solution for incident response but since i dont really have experience in that field its hard to really experience all the value it has to offer but im sure ill see it more clearly in the future and maybe this is a good time to look into practising more incident response type of stuff while using this tool. If i would have to recommend this to someone i think it would be to someone who actually uses these tools already and is looking for a better solution. I guess all cincan really needs from my perspective is more tools and making sure that all the tools have properly explained usage with the --help command.